Very good open source software to build your own OTP solution. It is called PrivacyIDEA. This product offers a lot of features :
- Authentication via a REST API with easy authentication with JWT.
- Returns easy parsable JSON output
- Can act as a SAML Identity Provider in conjunction with SimpleSAMLphp
- Plugins available for
- FreeRADIUS,
- PAM (supporting Offline OTP)
- Apache2,
- OTRS,
- Django,
- ownCloud,
- WordPress,
- TYPO3,
- Contao,
- dokuwiki…
There are two useful tutorials to help you to install and configure PrivacyIDEA :
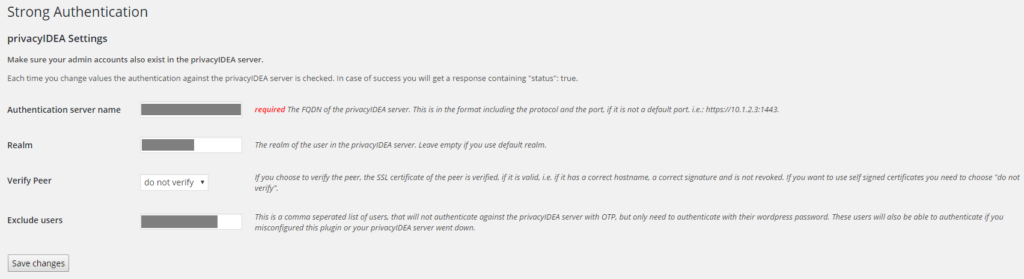
I have tested this solution for both Owncloud and WordPress. It is working well but be careful. There are several steps/configuration details that are not provided :
- for Owncloud : you will not be able to use PrivacyIDEA if you use Owncloud encryption module. The Owncloud encryption module uses your password : with PrivacyIDEA the password changes continuously. If you want to use PrivacyIDEA with Owncloud, you will have to decrypt and/or disable the server side encryption
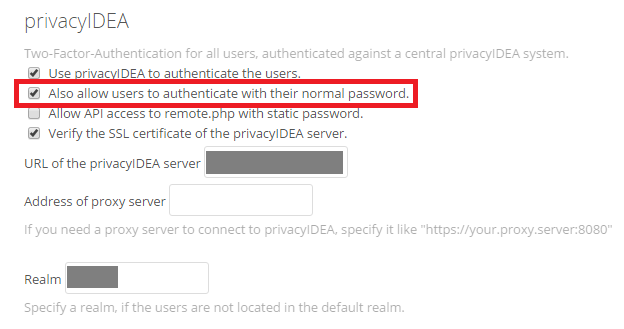
- for both WordPress/Owncloud : keep a standard user/password. You can configure on both environment an OTP exclusion for one or several specific accounts. It is important because if a PrivacyIDEA is not available you will not be able to login anymore.
Another tips for Owncloud : when you installed the PrivacyIDEA Owncloud app, unselect and select the tick “Use privacyIDEA to authenticate the users”. By default, just after you enable the app, this option is selected but the app will appear as disabled in the log file. Unselect/select this option enable properly the app.
Regarding the Apache configuration to host the privacyIDEA Web UI, you will have to adapt your configuration if you use virtual hosts. This is a vhost configuration example you can use to make it work properly:
################
# PRIVACY ID3A #
################
<VirtualHost *:443>
ServerAdmin webmaster@localhost
ServerName privacyidea.domain.local
DocumentRoot /var/www/privacyidea
<Directory />
Options FollowSymLinks
AllowOverride None
Require all denied
# restrict the access of the privacyidea admin console to limited ip address list
require ip 10.0.0.1 10.0.0.2 10.0.0.3
</Directory>
# I have added this section to make it work properly
<Directory /etc/privacyidea>
Order allow,deny
Allow from all
Require all granted
</Directory>
WSGIScriptAlias / /etc/privacyidea/privacyideaapp.wsgi
WSGIDaemonProcess privacyidea processes=1 threads=15 display-name=%{GROUP} user=privacyidea
WSGIProcessGroup privacyidea
WSGIPassAuthorization On
ErrorLog /var/log/apache2/error.log
LogLevel warn
LogFormat "%h %l %u %t %>s \"%m %U %H\" %b \"%{Referer}i\" \"%{User-agent}i\"" privacyIDEA
CustomLog /var/log/apache2/ssl_access.log privacyIDEA
SSLEngine on
SSLProtocol +TLSv1.2 +TLSv1.1 +TLSv1 -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-RC4-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:RC4-SHA:AES256-GCM-SHA384:AES256-SHA256:CAMELLIA256-SHA:ECDHE-RSA-AES128-SHA:AES128-GCM-SHA256:AES128-SHA256:AES128-SHA:CAMELLIA128-SHA !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4"
SSLCertificateFile /cert/yourcert.crt
SSLCertificateKeyFile /cert/yourcert.key
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
BrowserMatch ".*MSIE.*" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
</VirtualHost>
Last information, if you are using iptables/ip6tables rules with the default policy set to DROP, do not forget to add/permit the localhost communication with the mySQL database server:
ip6tables -I INPUT -i lo -p tcp -m tcp --sport 3306 -j ACCEPT ip6tables -I INPUT -i lo -p tcp -m tcp --dport 3306 -j ACCEPT iptables -I INPUT -i lo -j ACCEPT iptables -I OUTPUT -o lo -j ACCEPT
Do not hesitate to leave a comment if you have any questions or see something wrong in this article.
References
My Powershell script categories
- Active Directory
- Cluster
- Database
- Exchange
- Files and folders
- Hardware
- Network
- Operating System
- PKI
- SCCM
- Service and process
- Tips
- VMWare