
The “Local Administrator Password Solution” (LAPS) provides a centralized storage of secrets/passwords in Active Directory (AD) – without additional computers. Each organization’s domain administrators determine which users, such as helpdesk admins, are authorized to read the passwords. Source
Boe Prox has written a great article (read more on the author site) that describes how to implement LAPS and how to use Powershell to manage it.
First step is to install LAPS and select the modules
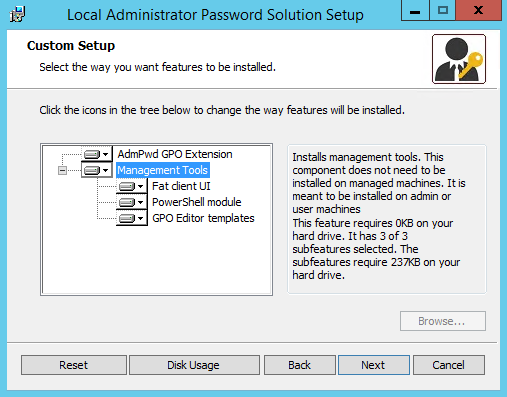
When done and before using LAPS, an Active Directory schema update is required. This schema update is done through the folowing commands :
Import-module AdmPwd.PS Update-AdmPwdADSchema
This schema update create and add two new attributes on every computer objects : ms-MCS-AdmPwdExpirationTime and ms-MCS-AdmPwd
Now let’s have a look on the newly installed cmdlets :
PS > Get-Command -Module AdmPwd.PS CommandType Name Version Source ----------- ---- ------- ------ Cmdlet Find-AdmPwdExtendedRights 5.0.0.0 AdmPwd.PS Cmdlet Get-AdmPwdPassword 5.0.0.0 AdmPwd.PS Cmdlet Reset-AdmPwdPassword 5.0.0.0 AdmPwd.PS Cmdlet Set-AdmPwdAuditing 5.0.0.0 AdmPwd.PS Cmdlet Set-AdmPwdComputerSelfPermission 5.0.0.0 AdmPwd.PS Cmdlet Set-AdmPwdReadPasswordPermission 5.0.0.0 AdmPwd.PS Cmdlet Set-AdmPwdResetPasswordPermission 5.0.0.0 AdmPwd.PS Cmdlet Update-AdmPwdADSchema 5.0.0.0 AdmPwd.PS
The description for each cmdlets are the following :
- Find-AdmPwdExtendedRights : Searches Active Directory tree for holders of CONTROL_ACCESS right on computer accounts
- Get-AdmPwdPassword : Finds admin password for given computer
- Reset-AdmPwdPassword : Requests reset of local admin password for given computer.
- Set-AdmPwdAuditing : Sets auditing for requests for passwords for local admin acocunts on computers in given container
- Set-AdmPwdComputerSelfPermission : Gives computers permission to report passwords of their local admin accounts to AD
- Set-AdmPwdReadPasswordPermission : Delegates the permission to read passwords of local admin account of computers in given container
- Set-AdmPwdResetPasswordPermission : Delegates the permission to request reset of passwords of local admin account of computers in given container
- Update-AdmPwdADSchema : Prepares AD schema for the solution
Some exmaples
#COMMON TASKS # get password of built-in admin on computer computername1. Get-AdmPwdPassword -ComputerName:computername1 # request immediate change of built-in admin password on computer computername1 Reset-AdmPwdPassword -ComputerName:computername1 #INSTALLATION TASKS #This command extends AD schema Update-AdmPwdADSchema #This command lists all security principals who are holders of All Extended Rights permission on containers in given container Find-AdmPwdExtendedRights -OrgUnit:AdmPwd # This command registers GPO CSE with given GPO. # GPO identity can be entered as displayName, GUID, or distinguishedName Register-AdmPwdWithGPO -GpoIdentity:AdmPwd # This command unregisters GPO CSE from given GPO. # GPO identity can be entered as displayName, GUID, or distinguishedName Unregister-AdmPwdWithGPO -GpoIdentity:AdmPwd # This command delegates SELF permission to read/write timestamp and write password on computer objects in given OU. This is required for GPO CSE to work properly # OrgUnit can be entered as name or distinguishedName Set-AdmPwdComputerSelfPermission -OrgUnit:admpwd # This commands delegated the right to read password and timestamp to given identity in given OU # OrgUnit can be entered as name or distinguishedName Set-AdmPwdReadPasswordPermission -OrgUnit:admPwd -AllowedPrincipals:MyDomain\MyIdentity # This commands delegated the right to reset password and timestamp to given identity in given OU # OrgUnit can be entered as name or distinguishedName Set-AdmPwdResetPasswordPermission -OrgUnit:admpwd -AllowedPrincipals:MyDomain\MyIdentity #This command sets up auditing of password reads Set-AdmPwdAuditing -Identity:AdmPwd -AuditedPrincipals:Everyone
You are now ready to read the article written by Boe Prox here
Local Administrator Password Solution with Powershell